Last week, a customer revealed a serious TerraMaster NAS vulnerability the company has yet to repair. TerraMaster claims their NAS systems are only available on a local network. As it turns out though, their NAS systems are accessible across the entire internet via the UPnP protocol. Universal Plug and Play (UPnP) is used by an infinite number of network devices, including NAS, routers, computers, gaming consoles, printers, mobile devices, IoT devices, and many more.
Last week, a customer revealed a serious TerraMaster NAS vulnerability the company has yet to repair. TerraMaster claims their NAS systems are only available on a local network. As it turns out though, their NAS systems are accessible across the entire internet via the UPnP protocol. Universal Plug and Play (UPnP) is used by an infinite number of network devices, including NAS, routers, computers, gaming consoles, printers, mobile devices, IoT devices, and many more.
Read More – 4 Steps for a Secure NAS

The vulnerability via UPnP may concede non-authenticated users, allowing them to remotely invade and extract your data, scan your local networks, or even make your devices participate in DDoS attacks. We reached out to Kevin Norman, the TerraMaster user behind this recent discovery. He shared with us his opinion on this exposure, additional details, and also some of the emails sent to the company, where he describes the findings.
What is UPnP?
First off, let’s consider an associated and traditional scenario; as we get readers from all the backgrounds and domains, it is important to start with the basics. Every time you plug a USB device, such as a mouse, keyboard, portable HDD, into your computer, you are using Plug and Play (PnP). Your device is instantly recognized in your whole computer; PnP saves you the hassle to do any additional configuration manually. Similar to PnP, Universal Plug and Play (UPnP) helps to detect any networked devices in your local network. It is intended (primarily) for residential and SOHO wireless networks. Typical scenarios are plugging a router, gaming system, NAS, or printer, where these devices will get recognized immediately by your personal computer and other devices.
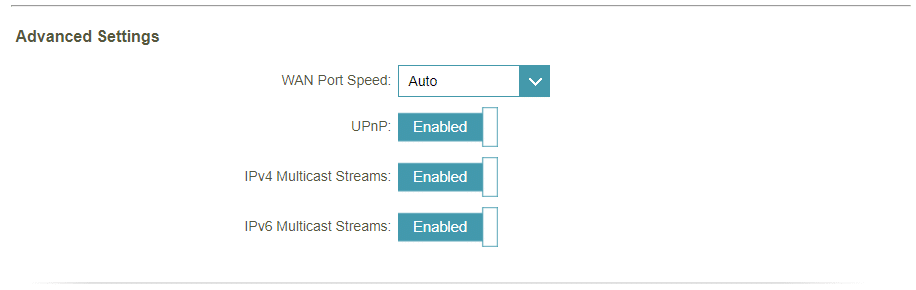
UPnP is handy, quickly allowing multiple devices to find clients over your local network. And just as PnP, it dramatically decreases the complexity of setting up new devices. However, UPnP can also be automatically adjusted by your router, allowing devices to access outside your local network. Using another popular protocol, Internet Gateway Device (IGD), a UPnP client can obtain the external IP address for your network and add new port forwarding mappings as part of its setup process. This method might sound interesting from a consumer perspective, but this benefit also exploits vulnerabilities and large-scale attacks. UPnP is essentially designed to be used in trusted local networks, where the protocol doesn’t need to implement any form of authentication or verification.
“The UPnP protocol, as default, does not implement any authentication, so UPnP device implementations must implement the additional Device Protection service, or implement the Device Security Service. A non-standard solution called UPnP-UP (Universal Plug and Play – User Profile) proposes an extension to allow user authentication and authorization mechanisms for UPnP devices and applications. Many UPnP device implementations lack authentication mechanisms, and by default assume local systems and their users are completely trustworthy.”
TerraMaster NAS Vulnerability Discovered Over UPnP
TerraMaster Technology Co., Ltd. is a Chinese company specializing in computer software, network-attached storage, and direct-attached storage. Recently, Kevin Norman published a blog post revealing a vulnerability in TerraMaster’s UPnP protocol that quickly widespread over Reddit and Hacker News. Kevin, a Software Engineer from the UK, said he reported his concern to TerraMaster in February of this year via email after running some tests independently.
Kevin found the UPnP vulnerability using a TerraMaster F2-210. The discovery waked his attention, probably, because of his awareness and concerns about using UPnP protocols, as he had stated and quoted on some other of his articles.
NAS, and many other network devices, are commonly administrated using a web interface, which is often the same GUI. In the case of TerraMaster, it uses TerraMaster Operating System (TOS) to operate the NAS. This OS requests you to access its GUI by visiting the NAS’s hostname on your network using port 8181. The system interface openly claims the NAS is not publicly accessible.
However, Kevin explains that after a few days of installing the NAS, he discovered he could reach it using his public IP, even though he hadn’t port forwarded anything. One more time, the GUI stated that the NAS was only accessible from the local network.
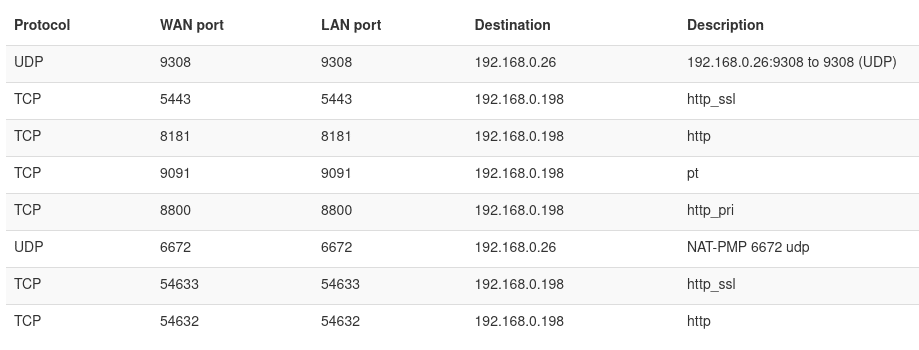
He inspected his router’s port forwarding rules, identifying that the NAS was exposing four ports using UPnP. It was not only exposed to the outside network via port 8181 but also port 5443. Other ports, Kevin said, include the 9091 and 8800, which he couldn’t find any explanation for. Port 9091 is generally used for Portainer, a container management tool for Docker, that he had not installed on the NAS.
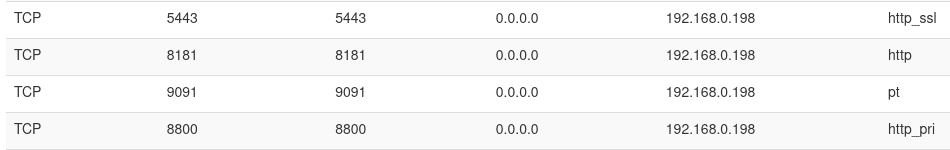
He guessed that TerraMaster developers were using these ports, and they possibly forgot to remove the config to punch them before releasing the software. “It seems that potentially some of these rules were left in from the development process.” Kevin commented, “I trust this NAS to be reliable hardware; however, I am dubious of trusting its web interface to the open internet. Generally, good practice to expose as little as possible to the public internet anyway!”
Besides, he tried to change the webserver port to something different as of 8181. The system forwards the new port but still leaves the old port exposed. Here is when he decided to contact TerraMaster to try to figure out what was going on.
TerraMaster Response and Workaround
Kevin contacted the company, but there were no recommendations to attend to or a fix from them to solve this issue promptly. Kevin went out on his own, finding root access to the router, which he used to dig out by himself. He remarks his appreciation to TerraMaster for at least providing root access.
After accessing via SSH into the NAS and using the root to explore the file system, it was discovered a file that could be modified. The “/etc/upnp.json” file shows to contains a list of port forwarding rules. A quick workaround from Kevin was to modify this file. He said: “Simply change bEnable to 0 for whatever ports you don’t want to be exposed, reboot the NAS, and check the port forwarding rules.”
“This almost completely resolves the problem; however, it seems the ports 8181 and 5443 remains punched but result in a 404 (error) since we moved the webserver earlier.” Kevin describes. “This is better than before, but still not perfect. I await further instructions from Terramaster/a software update”
Take into account that Kevin is a Software Engineer. And as many in the IT industry, he understands and is very familiar with networking, coding, and general IT concepts. But are many others that don’t. Regular users won’t be able to enter a system and modify advanced parameters, even after googling it.
Without entering into more technicalities, if you are really concern about this UPnP, you should disable it, at least until you do further research and consultation. Kevin also opted for this option at the end.
An Extended Opinion and Community’s Response
Following Kevin’s contact, he wrote back to us, and he was very kind to extend his opinion on this issue. He also wrote another blog post where he continues his opinion on this matter. After exposing and publishing the vulnerability, Kevin got several messages from the community, many supporting his point of view on UPnP and TerraMaster. Others didn’t agree.
He told us, and later also wrote in his blog, the following: “Some suggest disabling UPnP on your local router, but I personally believe this kind of misses the point. I am a Software Engineer who regularly dabbles in infrastructure (Kubernetes and the like) – and therefore, I have some idea of what I am doing. Therefore I ‘could’ disable UPnP. These NAS products aren’t really meant to be sold to people like me, I think, they’re more targeted to your average consumer, who wouldn’t have any idea what port forwarding or UPnP is.”
We agree with Kevin here, as we wrote and also explained in the above section.
He continued:
“Disabling UPnP definitely closes this particular security hole, but living in the real world for a second, the vast majority of consumer routers are going to have this feature on, and therefore the vast majority of these NAS products in the wild are likely exposing themselves unwittingly.”
“Others suggest buying a new router that would support having two separate LAN networks, so this NAS could be put on a LAN that is denied direct access to the internet/not have UPnP. This is even more ridiculous to expect consumers to do. I could do it, and very well may in the future, but I don’t really feel the need to upgrade my networking gear currently; it works, and I am happy with it, and again somewhat misses the point for the same reasons I detailed above.”
“This is why I went spelunking into the device itself. Thankfully TerraMaster provides root on these boxes, which is nice of them. This led me to discover the fix I did.”
He also attaches an extra discovery, by another TerraMaster user, on the NAS. Another exploit related to the TerraMaster, which was about leaking the admin password, was left in the Hacker News post comments. https://news.ycombinator.com/item?id=26683488.
The user “kotsec” claims:
“You should NOT have any TerraMaster NAS internet-facing right now. I disclosed a bug last month to TerraMaster that still hasn’t been fixed.”
“Go to http://NAS_IP/module/api.php?wap/ and it will give your admin password out as a md5crypt hash. Why? I assume it’s some sort of backdoor/dev code but I don’t know.”
So, Should You Use UPnP?
There should be nothing essentially wrong with the use of UPnP. However, it does appear that these protocols have a lot of security problems. This is not the first case reported about UPnP’s vulnerability; several more in the past years has been related to routers, other network devices, and local networks.
Usually, attacks on UPnP vulnerabilities are not likely to be performed against home users, but SOHO and SMB. Nevertheless, it could happen. In any case, the NAS should not be the device asking for forwards from the public internet. Kevin and other TerraMaster users are still waiting for a fix or patch to remediate this issue.
It seems the dilemma of disabling or not UPnP is entirely up to you; it is trading security for convenience. UPnP enabled in your router might expose many of your devices and applications to the internet, but at the same time, it will make it easier for you to reach them out remotely.
You should disable UPnP if you don’t plan to use applications that need port forwarding. Gaming consoles and servers, IoT devices, and peer-to-peer applications are the best examples nowadays. If you need any of these applications and still don’t desire to use UPnP, you can always perform manual (old-fashioned) port forwarding in your router. For what it’s worth, Kevin ended up disabling UPnP and seems happier for it.
Read More – 4 Steps for a Secure NAS
***Update 4-12-2021 – TerraMaster has issued a firmware update***
Engage with StorageReview
Newsletter | YouTube | LinkedIn | Instagram | Twitter | Facebook | TikTok | RSS Feed

