Actifio has commissioned IDC to research on how enterprises control their critical data, looking at copy data. The research found that two-thirds of companies failed to meet best practice standards for data control. With this study, Actifio is also announcing that it has seen dramatic growth in the number of its enterprise customers, as Actifio’s Virtual Data Pipeline technology is designed to better control and better enables access to critical data.
Despite well publicized, high-profile security breaches enterprises largely remain vulnerable to attacks were data copies can be used to gather confidential information. With production data growing geometrically, enterprises struggle keeping the data both safe and accessible. Part of the data protection generates massive amounts of copy data (that IDC estimates consumes up to 60% of the IT storage hardware and infrastructure budget), which in turn makes more targets to those that are attempting to access the data with malicious intent. Not only is this data difficult to protect, it is difficult for many companies to keep track of.
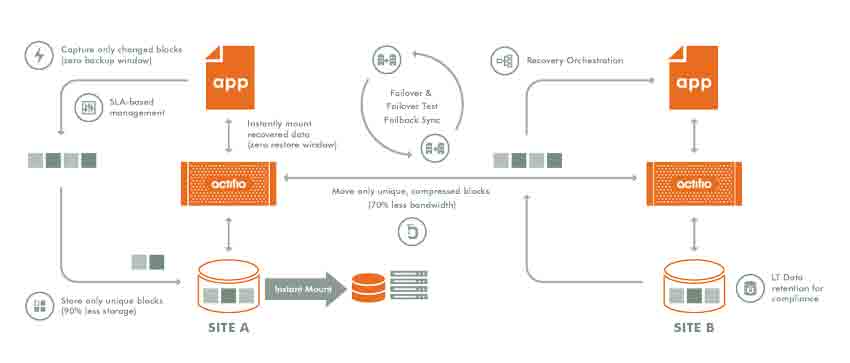
Actifio has seen an increase in its customers due to its ability to capture data directly from production applications, manage a single “golden master” copy of that data in their most secure environment, and then use virtual copies to maintain both accessibility and control. Virtualizing copy data limits its proliferation and availability.
Other findings of the study, “Common Gaps in Data Control: Identifying, Quantifying, and Solving Them Using Best Practices,” include:
- Two-thirds of enterprises fail to meet best practice standards for data control and few are likely to be consistent across the full spectrum of data security policies
- 77% of surveyed organizations fail to mask sensitive data during the test/development phase, which significantly increases the threat of a data breach
- Government performs best overall at implementing data control policies; the Education sector is the weakest
- The CIO is central to the implementation of data control/security policies – policies are only applied on an ad-hoc basis 34 percent of the time
- A typical organization holds 375 data copies, with each copy carrying sensitive information and therefore an increased risk of attack
Sign up for the StorageReview newsletter