 In an effort to help tamp down ransomware and other cyber attacks, Dell EMC announced the availability of its new Cyber Recovery software and Dell EMC Cyber Recovery Services. According to Dell EMC, its new software includes innovative automation, workflow and security analytics tools to ensure gold copies of critical data are isolated yet available so business processes can be resumed as quickly as possible in the event of a destructive cyber attack.
In an effort to help tamp down ransomware and other cyber attacks, Dell EMC announced the availability of its new Cyber Recovery software and Dell EMC Cyber Recovery Services. According to Dell EMC, its new software includes innovative automation, workflow and security analytics tools to ensure gold copies of critical data are isolated yet available so business processes can be resumed as quickly as possible in the event of a destructive cyber attack.
In an effort to help tamp down ransomware and other cyber attacks, Dell EMC announced the availability of its new Cyber Recovery software and Dell EMC Cyber Recovery Services. According to Dell EMC, its new software includes innovative automation, workflow and security analytics tools to ensure gold copies of critical data are isolated yet available so business processes can be resumed as quickly as possible in the event of a destructive cyber attack.
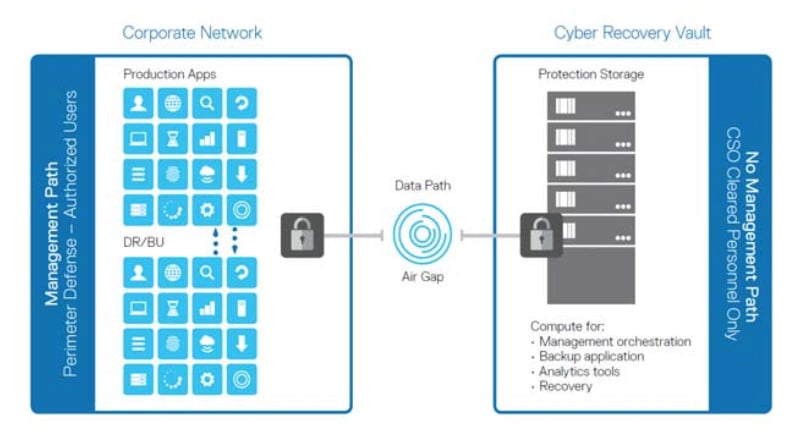
Cyber attacks and ransomware have unfortunately become common and are part of life for enterprises. Security is improving in most areas but companies still need a way to quickly recover lost data to avoid costly downtime. Dell EMC is addressing this with new software that combines data isolation with business continuity. This will minimize he impact of an attack and help recover critical data and systems faster. As stated above, Dell EMC Cyber Recovery uses automation to move and retain isolated secure copies of critical data to a Cyber Recovery vault. This removes the critical data from the attack surface. Once the data is in the vault it can be tested and analyzed without a restore eliminating the worry of activating any malware.
Along with the software, Dell EMC is releasing its Cyber Recovery Services to tailor fit customers needs in security.
Dell EMC Cyber Recovery Services include:
- Workshop: During this one-day workshop, consultants share Dell EMC best practices for business resiliency with a strong focus on cyber recovery.
- Advisory: The advisory service builds on the Workshop by adding development of a high level cyber recovery strategy. The customer’s current and desired state is analyzed to create a tailored strategy for cyber recovery preparedness.
- Advisory & Roadmap: The advisory & roadmap builds on the advisory service with a deeper dive into customer’s cyber recovery strategy to recommend an optimized implementation roadmap. This includes developing a cyber recovery maturity model report, which benchmarks the customer’s current state against industry best practices. Also included is a critical materials workshop and information session to collect data on the customer’s applications to understand criticality to the business. These considerations will help drive recommendations of data and applications which should be protected by the Cyber Recovery Vault.
- Deployment: New deployment services help maximize the capabilities of Dell EMC Cyber Recovery Solutions. They can be added to the ProDeploy Enterprise Suite or purchased separately and are available in two variations to fit customer needs.
- Implementation: Dell EMC Services can also customize the implementation of the Cyber Recovery Solution to account for a variety of additional use cases. This can include hardening of additional Dell EMC technology, developing detailed operational procedures and implementing custom dashboards and reporting.
Availability
Dell EMC Cyber Recovery software and Dell EMC Cyber Recovery Services are available now.
Sign up for the StorageReview newsletter
