In the last few months, it would seem that the evildoers that leverage ransomware to make money have turned their focus to NAS devices. The most recent example we saw was with QNAP and the Qlocker attack. Though TerraMaster recently had a security fault come to light and Synology was suffering attacks a few years back. Most likely, when the first attacks are successful, attackers are just going to keep it up. Luckily, there are steps users can take to mitigate these attacks, netting a more secure NAS.
Why Attack NAS Devices?
So, the question is, why are NAS devices under attack as of late? Well, these devices, particularly Synology and QNAP, are all about simplicity. Someone with little to no IT experience can set up a NAS and start using it with essentially no training. While this makes it nice for home users and small businesses with no IT resources, it also leaves lots of gaps in security. Ultimately it is a tradeoff. The easy setup comes at the cost of potential security issues. Also, NAS platforms are more or less self-hosted clouds these days, staying connected 24/7 leaves them open for an attack (if you aren’t online, you can’t be hacked remotely). W
Let’s Backup For a Minute
One of the most important steps users can take is to back up their data. Most NAS offer some sort of backup to offsite. Full backups can be resource-heavy but can be done when system access is low. Storing backups to the cloud is usually not as expensive as retrieving the data, but it is better to pay one of the public clouds for retrieving your data than paying a ransom. Both Synology and QNAP offer snapshots as well or you can leverage something like Veeam for NAS backup. Restoring from an air-gapped external backup is the easiest way to fix ransomware issues, but that doesn’t solve the attack vector behind the offense in the first place.
Secure NAS Step 1: Disable Console Access
As we said, most modern NAS are tiny little clouds. This is good for ease of use, but bad for security. The first step we need to take is buttoning them up to move toward a more secure NAS. This is done by disabling telnet and SSH so there is no longer console access.
For a QNAP you would go to Control Panel>Security>IP Access Protection. Power users love console access, it is a big door open that doesn’t need to be if not in use.
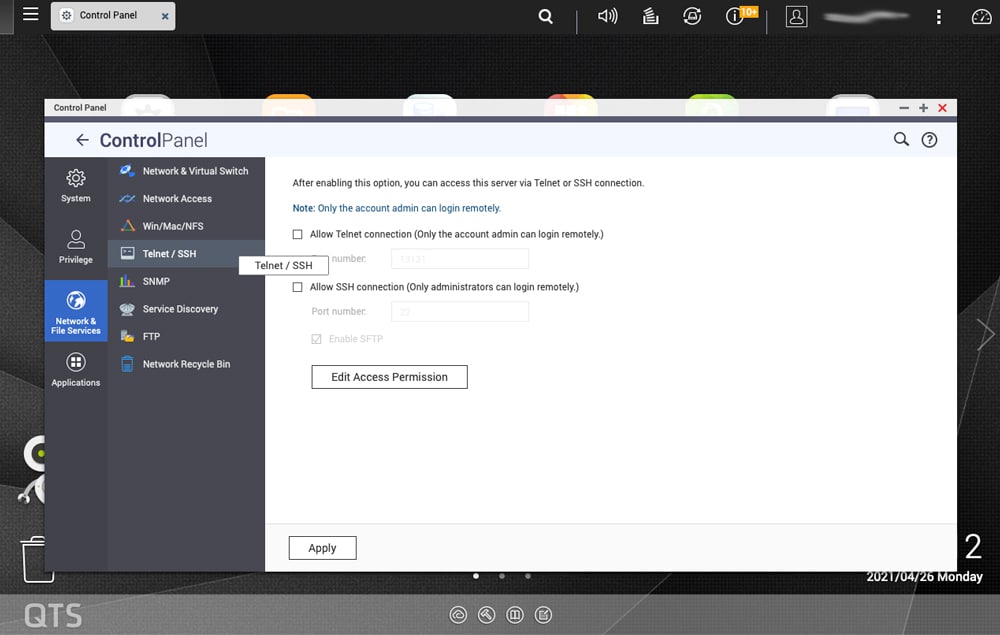
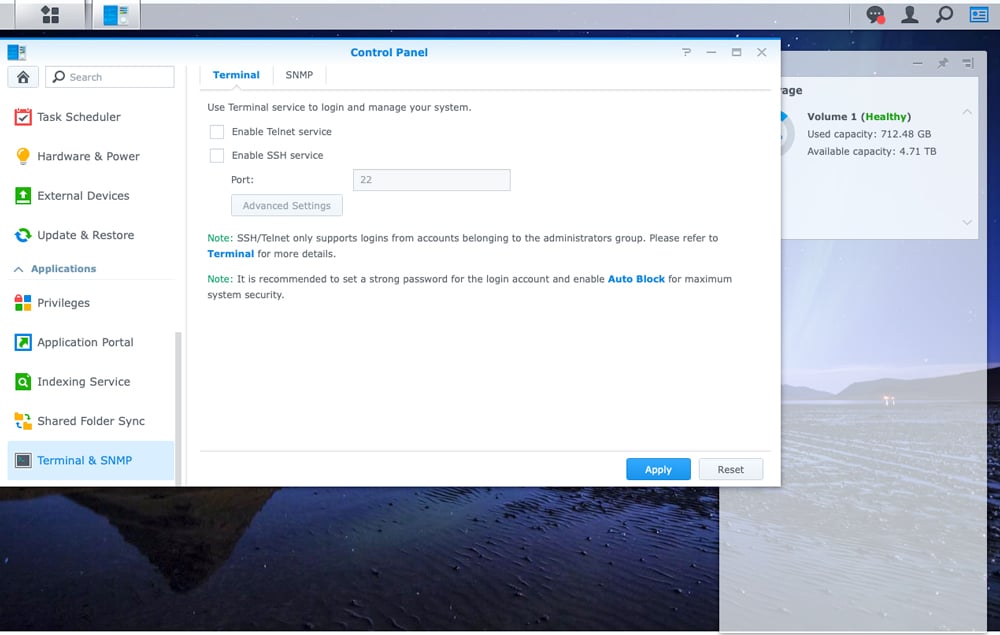
For a Synology, you would go to Control Panel>Terminal&SNMP>Terminal. Here, you can disable SSH and telnet.
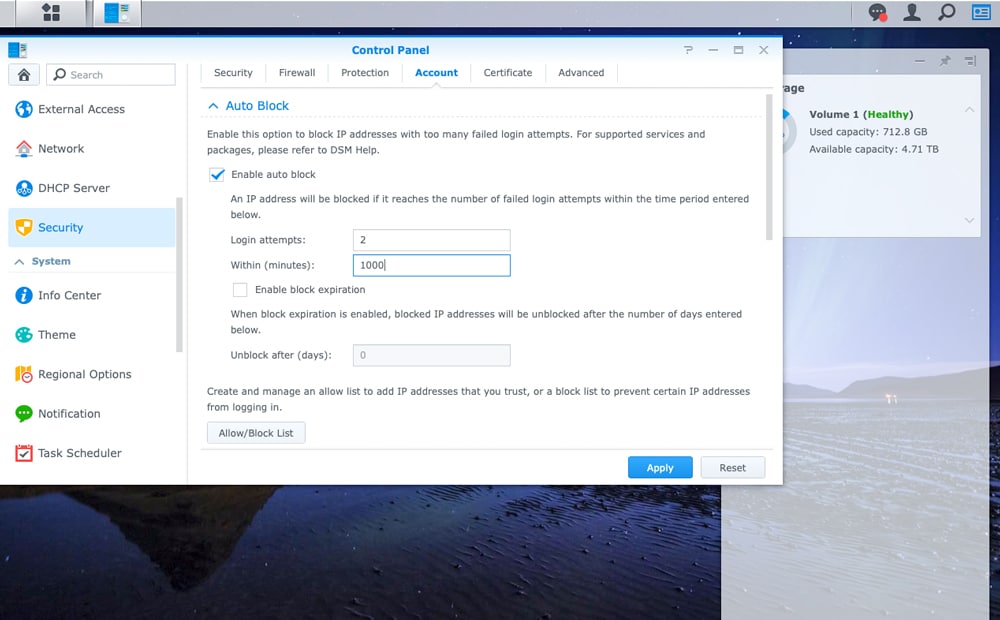
Secure NAS Step 2: Turn on Auto Block
People would be surprised to learn how often NAS devices are “hacked” by someone just guessing the username and password. Most access these days are just bot-farms guessing passwords over and over in brute force attacks. An easy way to prevent this, and to move one step closer to a secure NAS, is by turning on auto block.
Auto block will block an IP address with too many failed login attempts. Users can set up how many attempts they want to allow (keep in mind you may enter the wrong username and/or password yourself). A way we like to deploy Synology in the wild is two failed login attempts over 5000 minutes and you are banned forever. The only fix is logging in locally to the NAS and removing that IP from the blacklist.
For Synology, you would just go to Control Panel>Security>Account. Auto Block should be right at the top. Enable it and then put in the attempts you want to allow within a time frame to trigger a block.
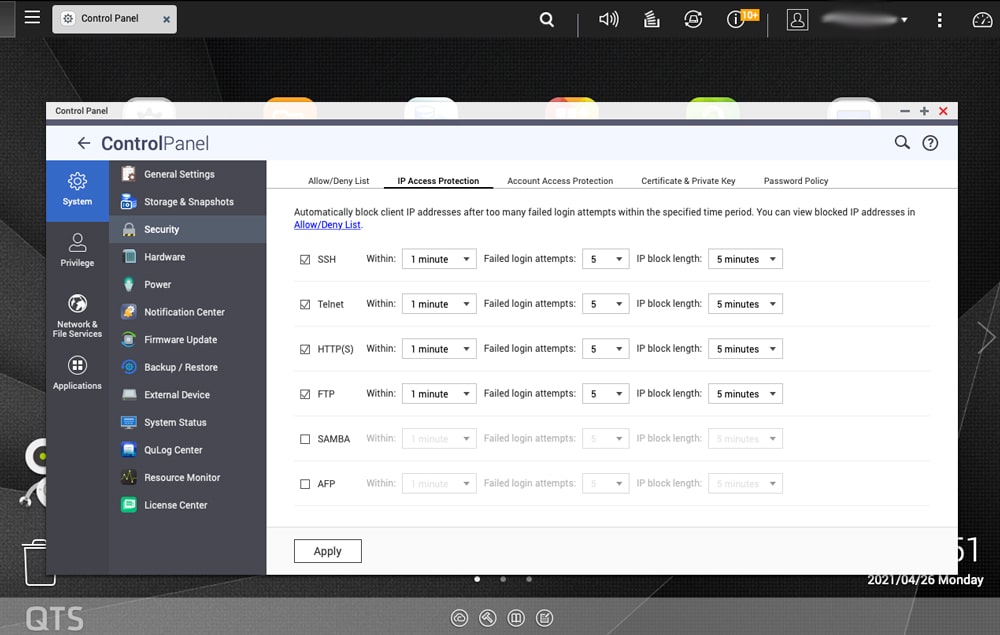
With QNAP one needs to go to Control Panel>Security>IP Access Protection and set up the attempts there.
Secure NAS Step 3: Disable Remove Unused Apps
About a decade ago, there was a marketing campaign telling us that there was an app for everything (or rather someone would say something followed by, there’s an app for that). Now there is and there are tons of apps clogging up our phones, tablets, and now our NAS devices.
Lots of this stuff is free and cool and if we just had an extra 30 minutes a day, we would do something with it. But we don’t. Unused apps (some of dubious quality and vetting) on your NAS should be removed or disabled to prevent any security threats.
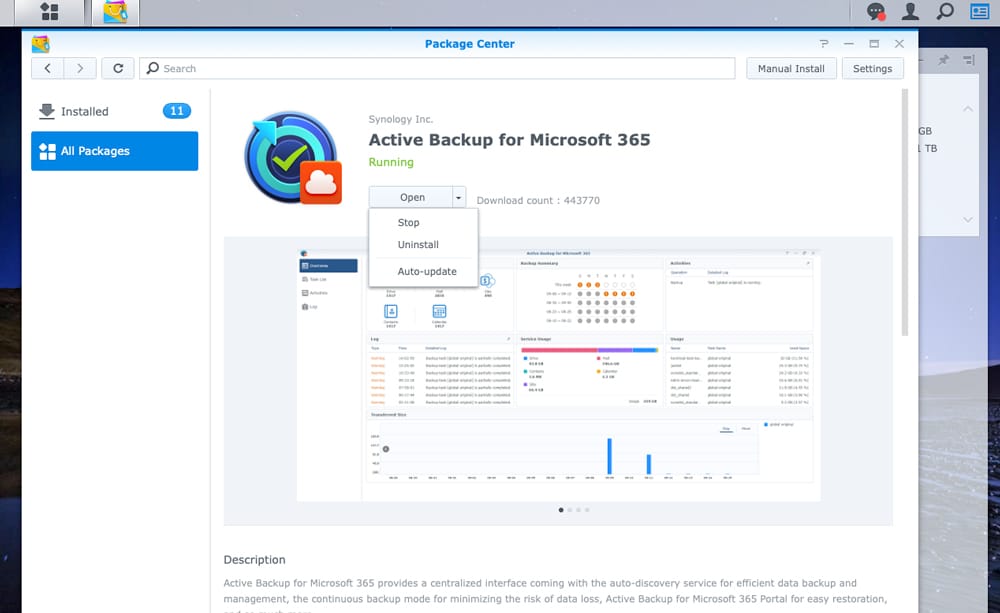
With Synology, you simply need to go to the Package center, click on the app, and there is a drop-down next to the Open where you can choose Stop or Uninstall.
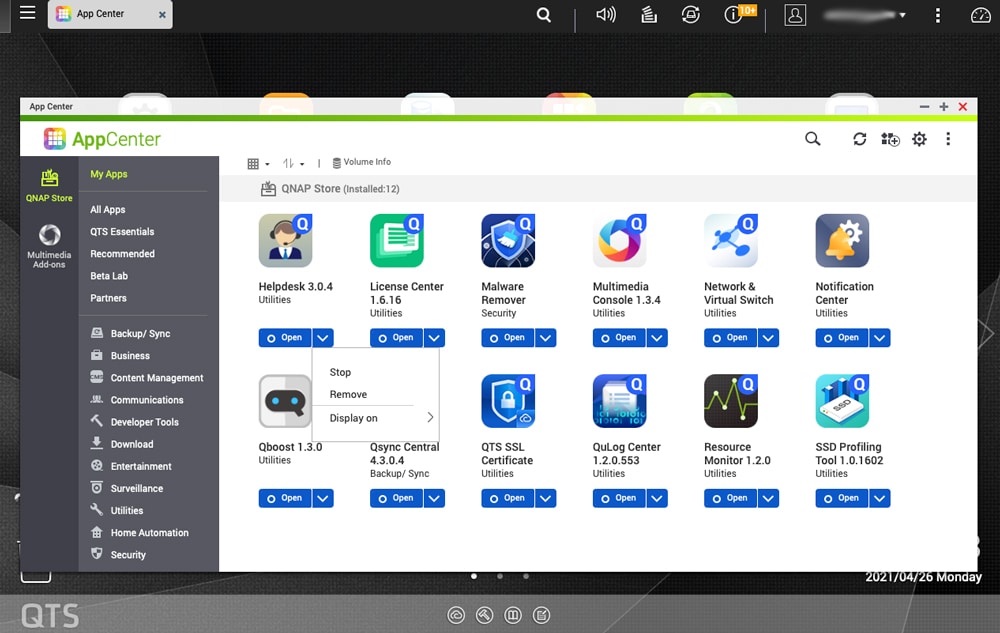
For QNAP go to the App Center and open the drop-down menu next to the app you wish to stop or remove.
Bonus: Don’t Use Admin as a Username
This one seems easy, but very few people do it at home or even in the data center. When you set up either a NAS it creates a default account, usually with “Admin” as the username. Most people leave that and just change the password. It’s a nice feeling, thinking I am The Admin. But this just takes some of the work away from nefarious actors and is the easiest of all when it comes to making a secure NAS.
One solution is to create a new user with your credentials and then delete or disable the original admin account. Or sometimes you can rename the Admin account to something else. Either way, by removing username from the equation hackers have to work much harder to guess both the username AND password.
Closing Thoughts
Ransomware attacks against NAS systems are on the rise but you can take steps to protect yourself by deploying a more secure NAS. The above won’t guarantee you will be safe from a ransomware attack, but they will surely help a lot.




 Amazon
Amazon