Over the past few days, users of QNAP systems’ devices have been hit with a ransomware attack. In fact, two we discovered, Qlocker and eCh0raix. These attacks do what the usual ransomware buttholes do and encrypt users’ data while offering to give it back for a fee. QNAP is on the ball and has released an updated Malware Remover. We’re going to quickly go through and show users how to scan for Malware on the QNAP Devices and remove it.
Over the past few days, users of QNAP systems’ devices have been hit with a ransomware attack. In fact, two we discovered, Qlocker and eCh0raix. These attacks do what the usual ransomware buttholes do and encrypt users’ data while offering to give it back for a fee. QNAP is on the ball and has released an updated Malware Remover. We’re going to quickly go through and show users how to scan for Malware on the QNAP Devices and remove it.
Read More – 4 Steps for a Secure NAS
Qlocker Ransomware What We know
Ransomware is a type of malware that gets into users’ files and either threatens to publish them publicly or encrypts them and keeps the owner from getting access to them. In either case, the perpetrator asks for a ransom to unlock the data. These types of attacks have really blown up in the last decade or so, doubling in 2020 from 2019. This is something that all the major and minor vendors struggle with and will going forward. This is why backing up your data and keeping it separate is always a good idea, also leverages snapshots when possible.
From user reports over the last few days, Qlocker seems to have begun targeting QNAP devices worldwide a few days ago on April 19th, 2021. According to BleepingComputer, the attackers are using 1-zip to move files on the affected QNAP devise into password-protected archives. Once finished victims get a read me ransom note with some variation of the following:
!!! All your files have been encrypted !!!
All your files were encrypted using a private and unique key generated for the computer. This key is stored in our server and the only way to receive your key and decrypt your files is making a Bitcoin payment.
To purchase your key and decrypt your files, please follow these steps:
This is followed by where to go and where to enter the key, which one gets by paying.
QNAP’s Ransomware Response
QNAP did the right thing and openly addressed the issue earlier this morning. Making people aware there is an issue, is typically a fast way to get them to pay attention and potentially avoid it. Not only did the company talk about the ransomware, but they also released a new Malware Remover for QNAP NAS devices.
QNAP is urging both those affected and unaffected to scan for malware and to update the Multimedia Console, Media Streaming Add-on, and Hybrid Backup Sync apps. Also, users should all change their passwords to stronger passwords. Right now, they don’t have a solution for the infected devices but urge victims to contact their technical support.
QNAP Malware Remover Walkthrough
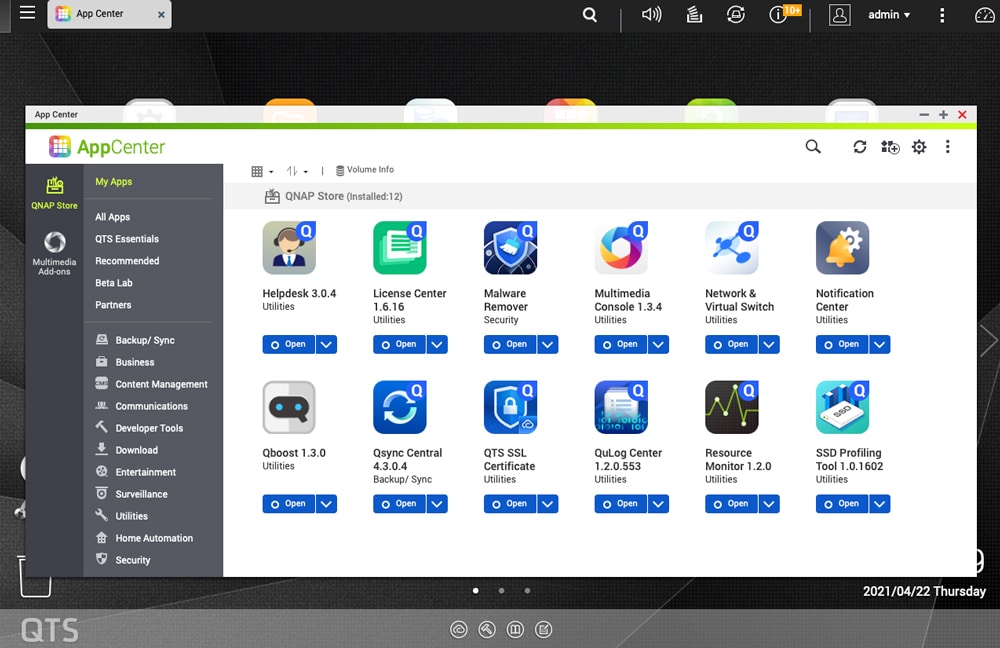
Once you are signed into QTS, go to the App Center and check the version of Malware Remover and update it if needed.
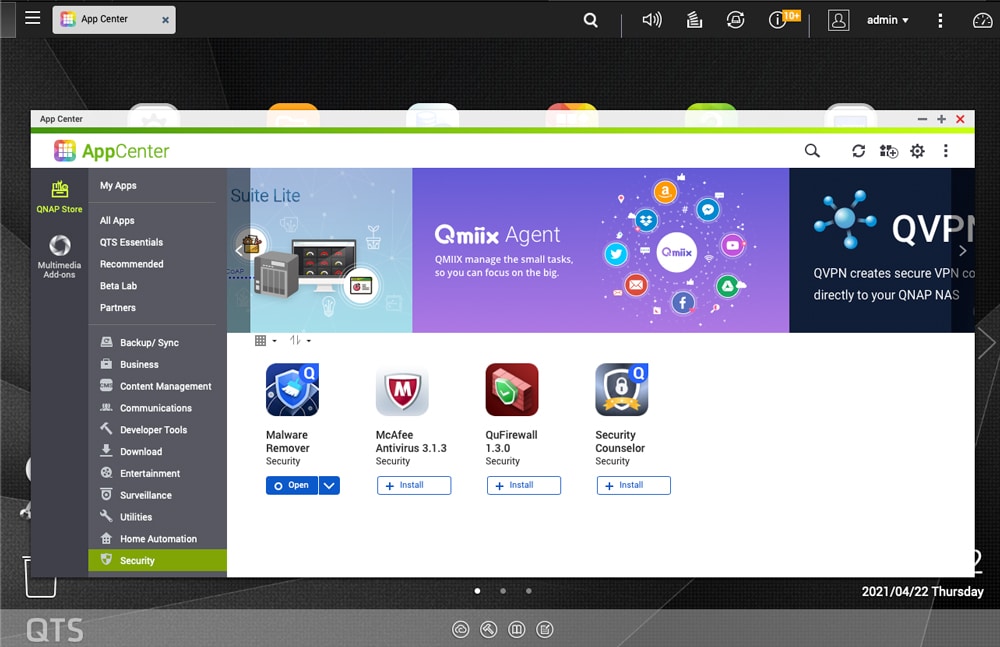
If you haven’t yet downloaded Malware Remover, it is in the security section of the App Center.
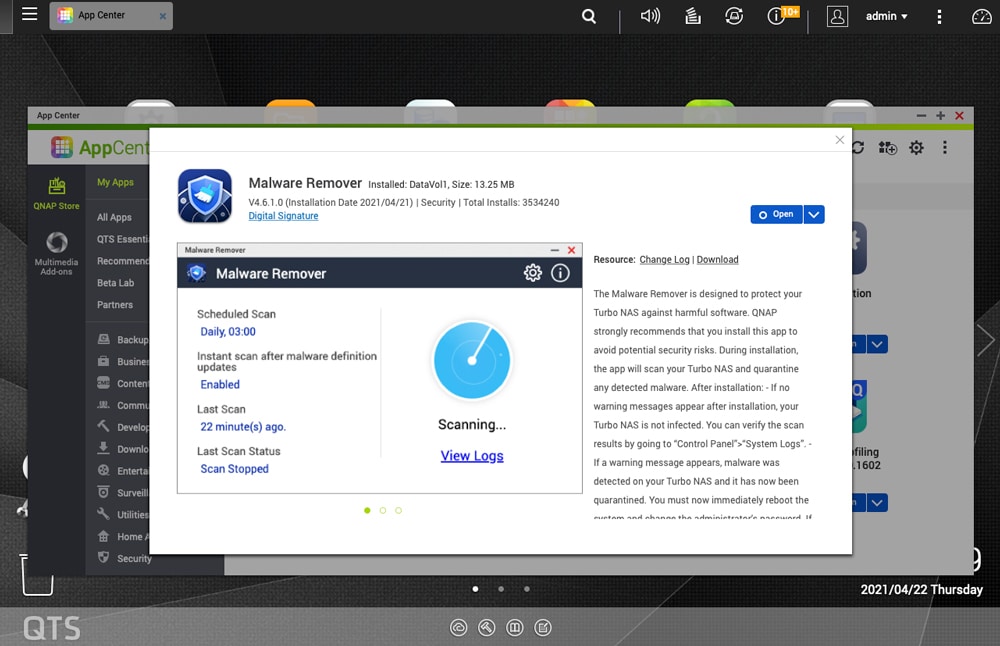
Clicking on it should give you the option of updating as well. Once updated click open.
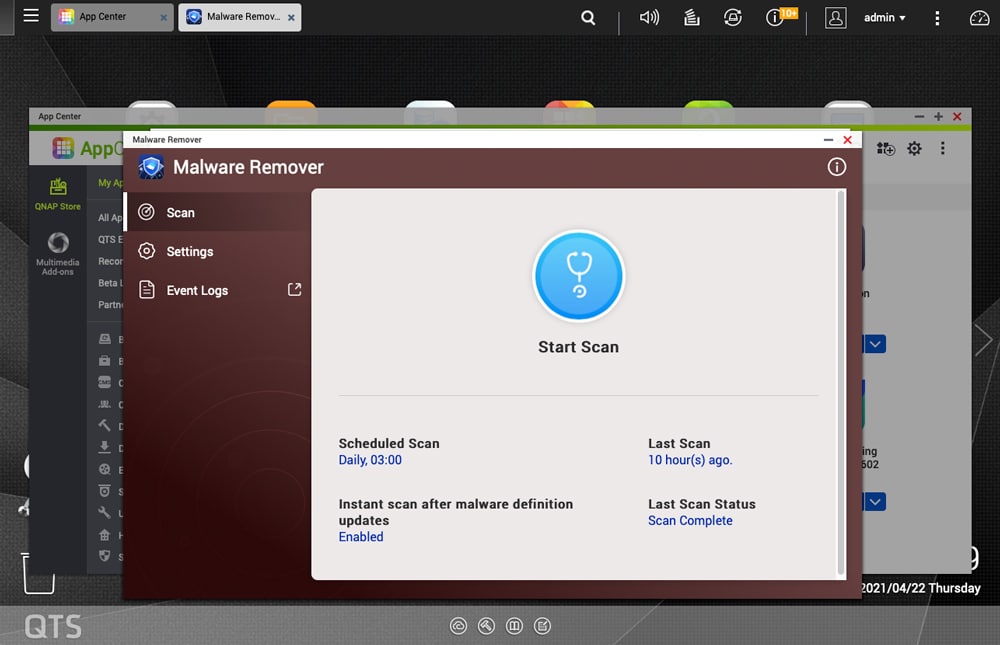
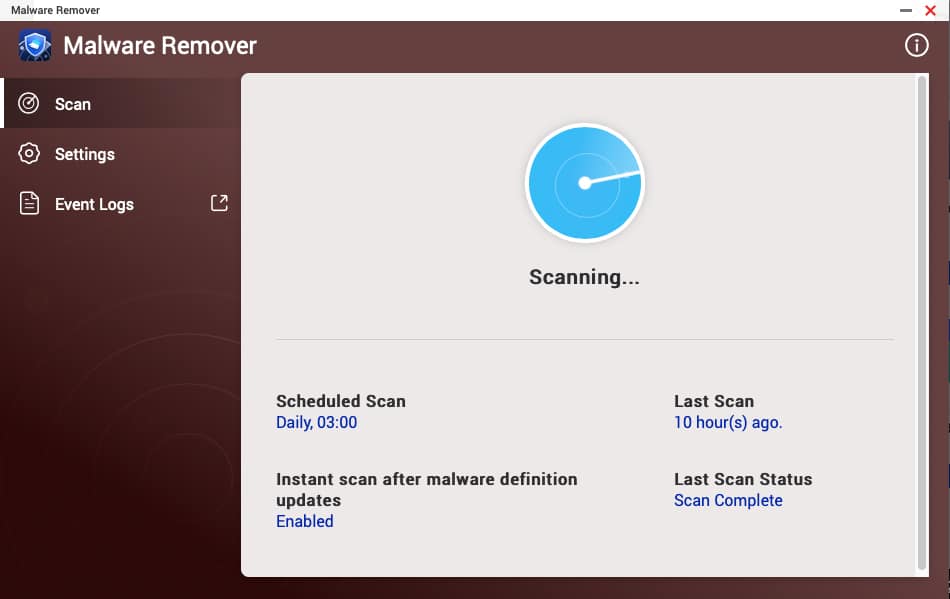
Once open you will see what looks like a stethoscope slightly floating around. Click on that guy and let it do its thing.
In our case, it only took a few minutes but this can vary by your NAS model and what is on the device.
And that is it. If it finds something, particularly the new ransomware it will remove it.
Closing Thoughts
QNAP users are being hit with the new Qlocker Ransomware but the company is trying to stay on top of it. They don’t have a remedy for those affected just yet, but the steps above will get you on the right path. As always, it is important to backup important data and move it offsite or at least off of the NAS so if something happens, like this, you can restore from backup and be back on your way. Of course, this isn’t isolated to QNAP, all NAS systems are under attack, TerraMaster recently was hit as well.
Another good tip is not presenting your NAS to the internet if not required, since if you don’t leverage a lot of the remote features anyways, you are increasing your risk for no benefit. And if you don’t use a QNAP NAS, you may want to backup anyway. QNAP is being struck at the moment, but they won’t stop here.
Read More – 4 Steps for a Secure NAS
Engage with StorageReview
Newsletter | YouTube | LinkedIn | Instagram | Twitter | Facebook | TikTok | RSS Feed