Ubiquiti has launched their UniFi Network 9.0.92 Early Access update, introducing the Zone-Based Firewall (ZBF). This significant upgrade empowers administrators with a simplified yet powerful toolset for managing network security. This update concerns gateways and cloud gateways, which we’ve deployed on the Cloud Gateway Ultra through the Dream Machine Pro Max.

This innovation focuses on grouping interfaces, such as VLANs, WANs, and VPNs, into logical zones, allowing for more intuitive policy creation, better segmentation, and heightened security.
Key Features and Benefits
Simplified Policy Management
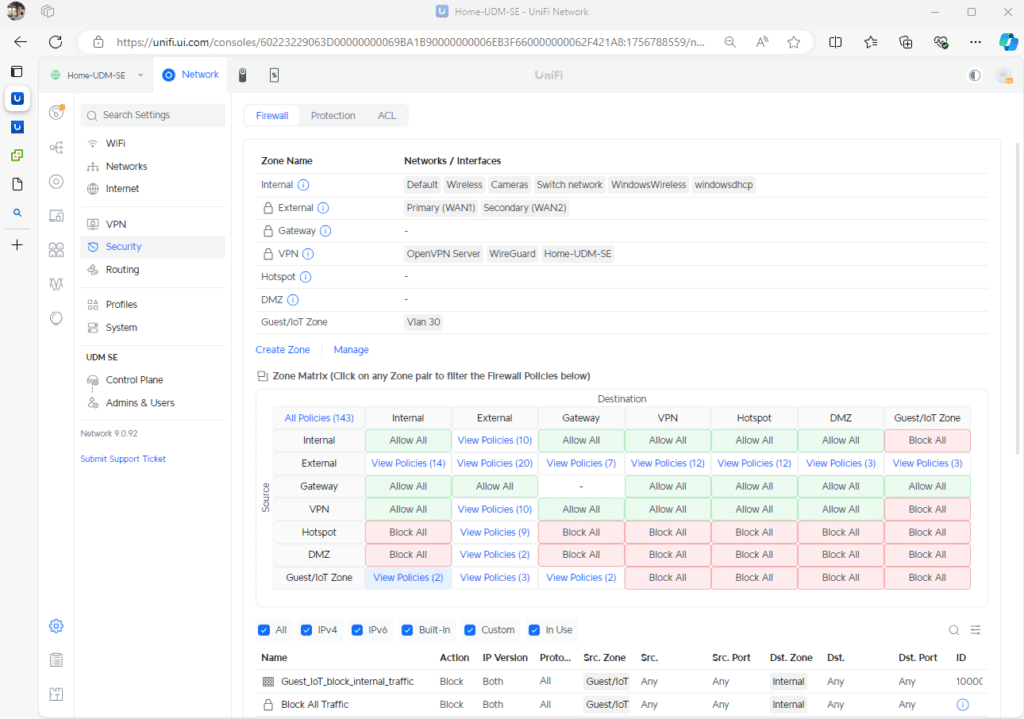
Gone are the days of per-interface configurations that could become unwieldy in complex networks. The new Zone Matrix offers a clear visual representation of traffic flow between zones, enabling administrators to assess and modify security policies quickly. This intuitive approach makes policy management more accessible, even for less experienced network administrators.
Enhanced Network Segmentation
UniFi’s ZBF introduces predefined zones, including Internal, External, DMZ, VPN, and Hotspot, each tailored to common security needs. These zones ensure granular control over traffic flows, allowing administrators to apply specific rules to different network elements. This design helps isolate IoT devices, secure sensitive data servers, or manage guest traffic without risking the internal network.
Custom Policies for Flexibility
While predefined rules streamline setup, the custom policy feature allows administrators to tailor security settings to unique organizational requirements. Whether blocking a specific protocol, creating exceptions for trusted devices, or prioritizing traffic types, the flexibility of custom policies ensures that the ZBF can adapt to even the most complex network environments.
Visibility and Control
The ZBF includes built-in rules to safeguard critical flow, such as DHCP and DNS traffic to the gateway, ensuring that essential services are not accidentally disrupted. Enhanced logging capabilities through syslog provide detailed insights into traffic patterns and potential threats. Additionally, administrators can easily reorder rules to reflect changing priorities or requirements, improving oversight and adaptability.
Practical Applications of (ZBF)
The ZBF framework is designed to reduce complexity while strengthening security, making it a valuable addition for organizations of all sizes.
Securing IoT Networks
IoT devices often have limited built-in security, making them vulnerable to attacks. With ZBF, administrators can place all IoT devices in a dedicated zone and create policies that:
- Block IoT devices from accessing sensitive internal networks.
- Allow IoT devices to communicate only with specific external services or resources.
Isolating Guest Traffic
Guest users can be restricted to a dedicated zone that only permits internet access, preventing them from interacting with internal devices or sensitive data.
Balancing Internal and External Traffic
Predefined “Internal to External” policies offer a balanced approach, granting secure internet access to internal users while maintaining robust safeguards against potential threats.
Advanced Customizations
Organizations can create additional zones for specialized needs, such as segregating developer environments, testing labs, or remote VPN users, ensuring fine-grained control over inter-zone communication.
Considerations for Deployment
While ZBF simplifies firewall management, careful planning is essential to avoid unintended consequences. Administrators should:
- Understand Zone Behavior: Moving networks between zones or blocking traffic to the gateway (critical for services like DHCP and DNS) can disrupt operations if not managed carefully.
- Audit Traffic Flows: Before implementing ZBF, review current traffic patterns to ensure that essential communication paths are preserved.
- Test Rules: Gradual testing of new rules helps prevent widespread disruptions, especially in larger environments with mixed trust levels.
- Leverage Logging: Use logging features to monitor the impact of changes and identify areas for refinement.
ZBF Configuration Example
UniFi’s Zone-Based Firewall (ZBF) is a significant step in simplifying and enhancing network security. Shifting from traditional per-interface configurations to a zone-based approach enables administrators to focus on intentional security outcomes rather than wrestling with complex setups. Its intuitive design and robust customization options make it ideal for small-scale and enterprise deployments.
To illustrate its practical implementation, the following is an example of how to set up a new Guest/IoT Zone using UniFi’s ZBF in the latest update. The goal was to isolate guest and IoT devices, ensuring they had controlled access to external resources without jeopardizing internal security.
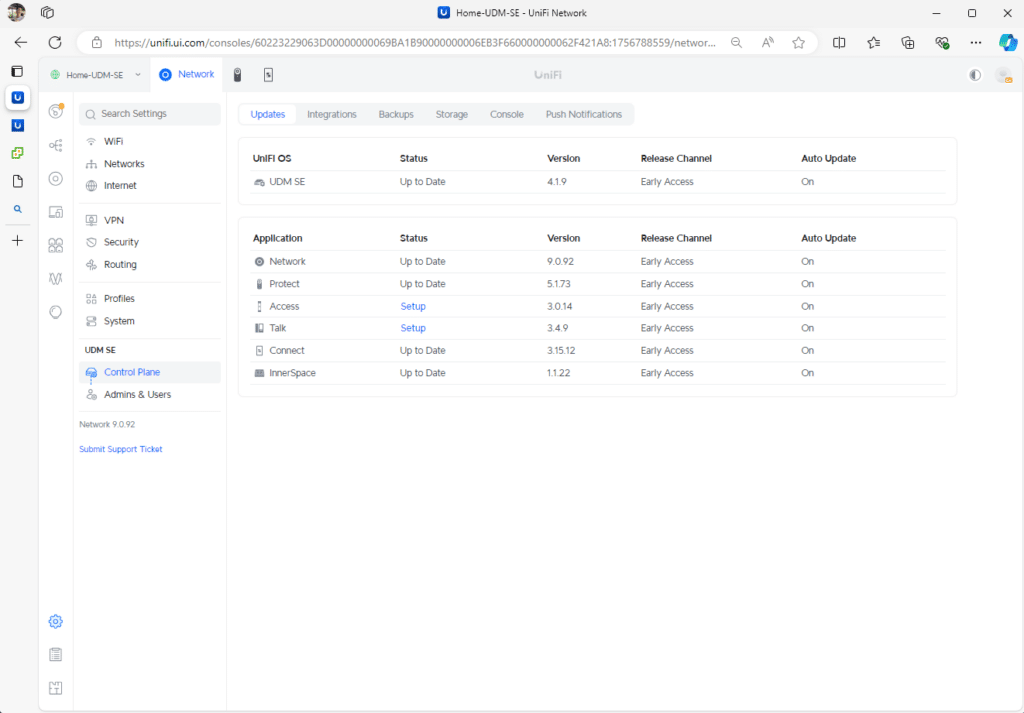
Update to the EA Release
Follow the steps below to update to the EA Release Network 9.0.92.
-
- Go to Settings > Control Plane > Updates in UniFi Controller.
- Click Check for Updates or Update and install the latest EA version.
- Enable Early Access in the same menu if not already enabled.
Next, enable Zone-Based Firewall (ZBF) by following the steps below.
- Go to Settings > Firewall & Security.
- Enable Zone-Based Firewall.
- Configure zones and set traffic policies using the Zone Matrix.
Zone Configuration example
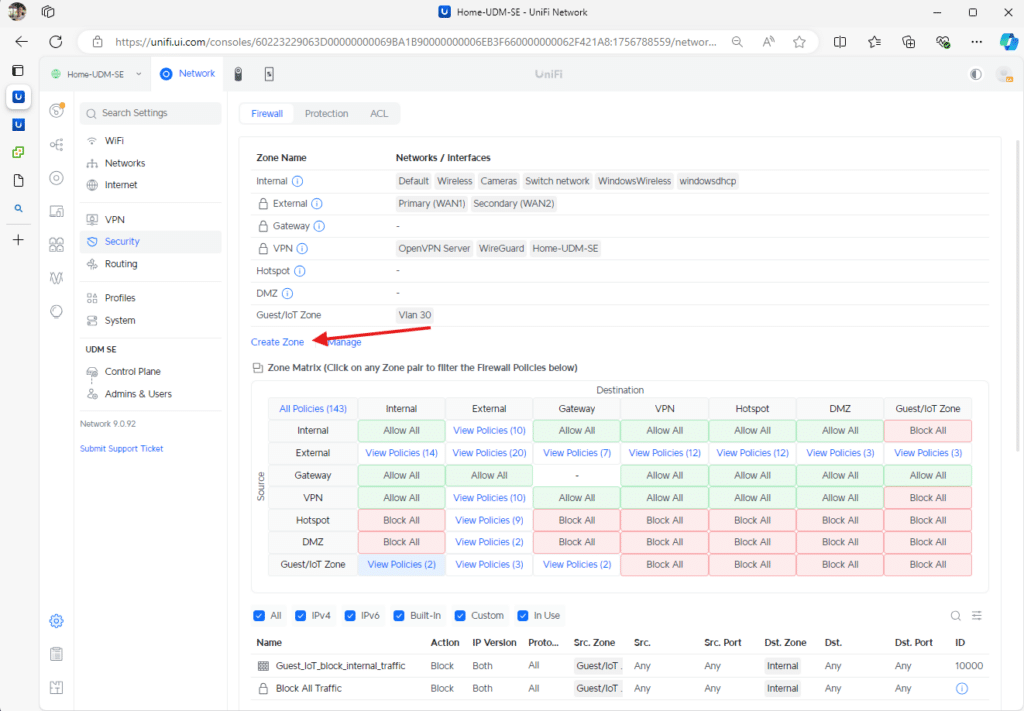
Start by creating a new zone. First, view the default zones, then click the Create Zone option.
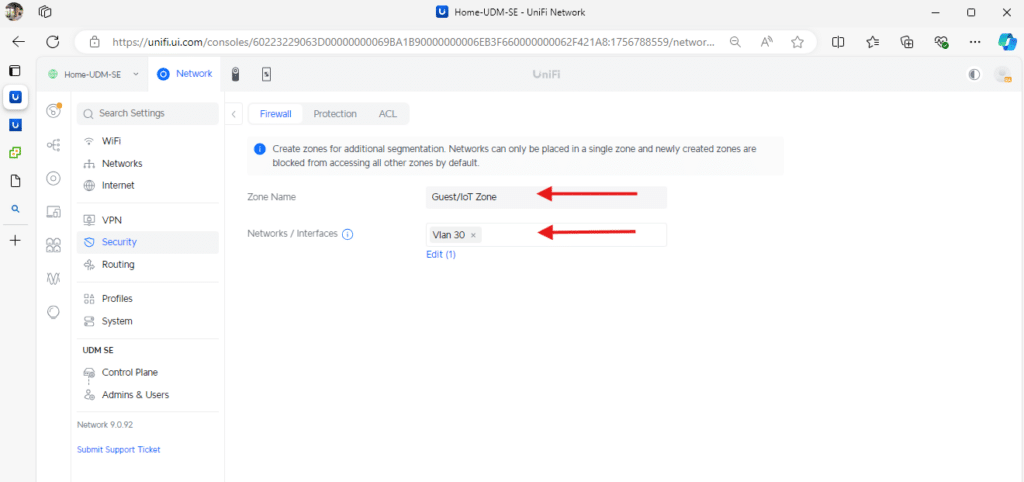
Clicking Create Zone will take you to the configuration screen to set up the new zone. For this example, we named it Guest/IoT Zone. It’s important to ensure a VLAN is created or is pre-existing before associating it with this new zone. In our example, we used VLAN 30. Any pre-existing rules tied to this VLAN or network might be paused or removed when creating the new zone.
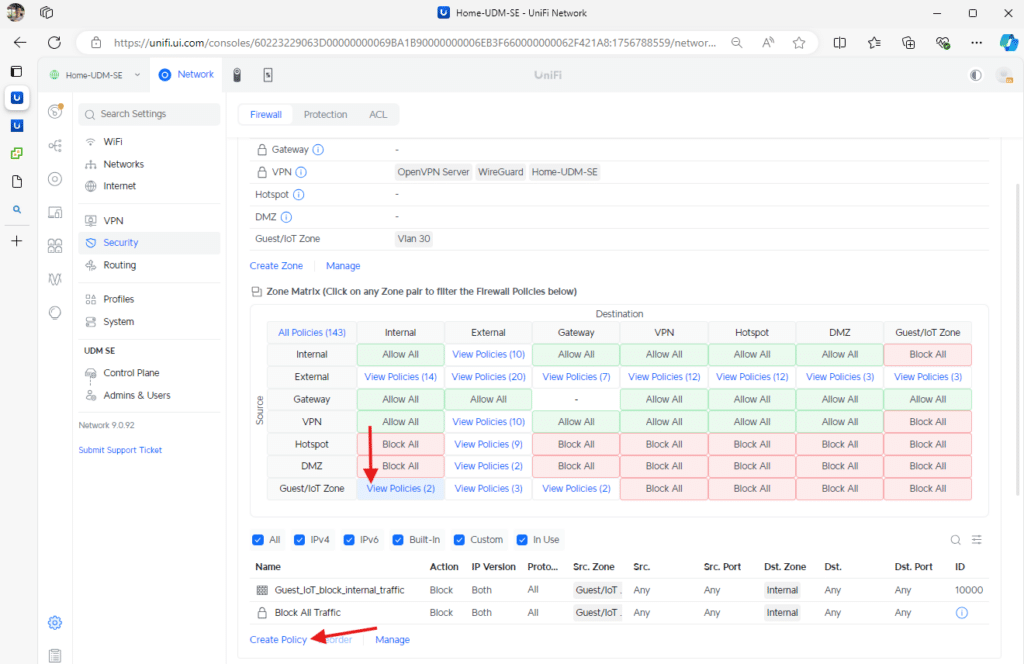
After setting up the zone, return to the main page by clicking the back button in the top-left corner. You’ll need three firewall rules to create an isolated Guest/IoT network that only allows internet access while blocking local device communication.
First, click on Manage. Alternatively, you can filter to the Guest/IoT Zone row and select the first option in the Internal column. This will also display any related rules associated with this zone on the interface.
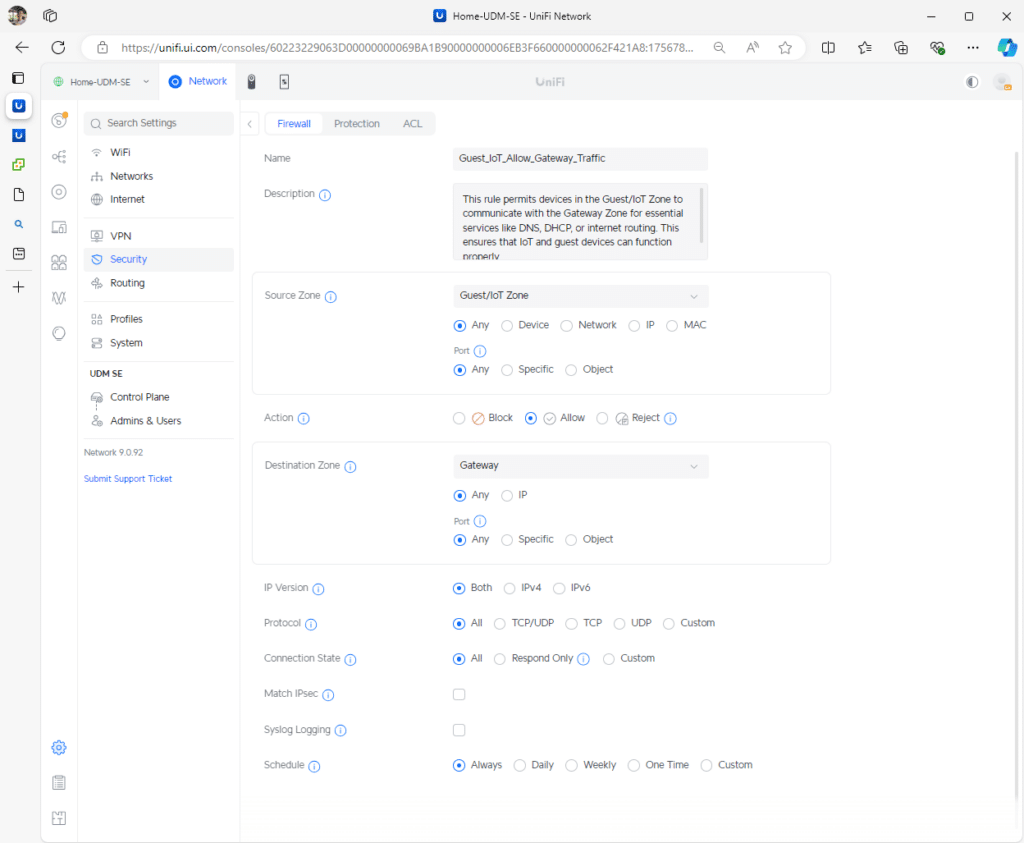
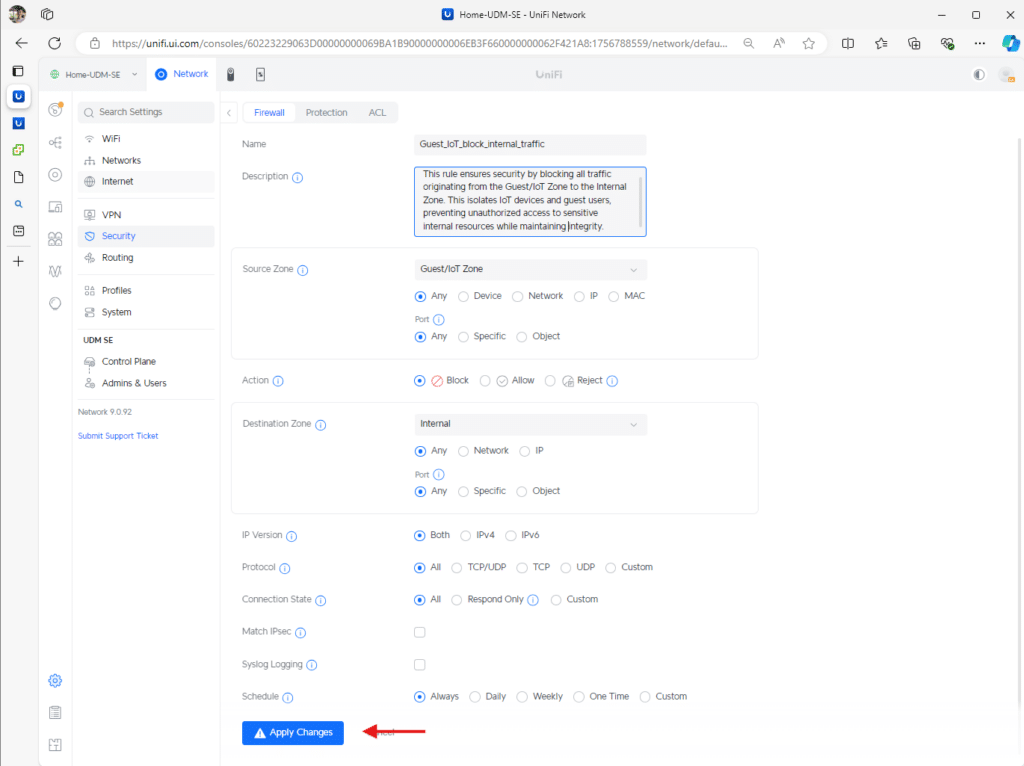
Rule1: Block IoT/Guests from accessing the Internal zone.
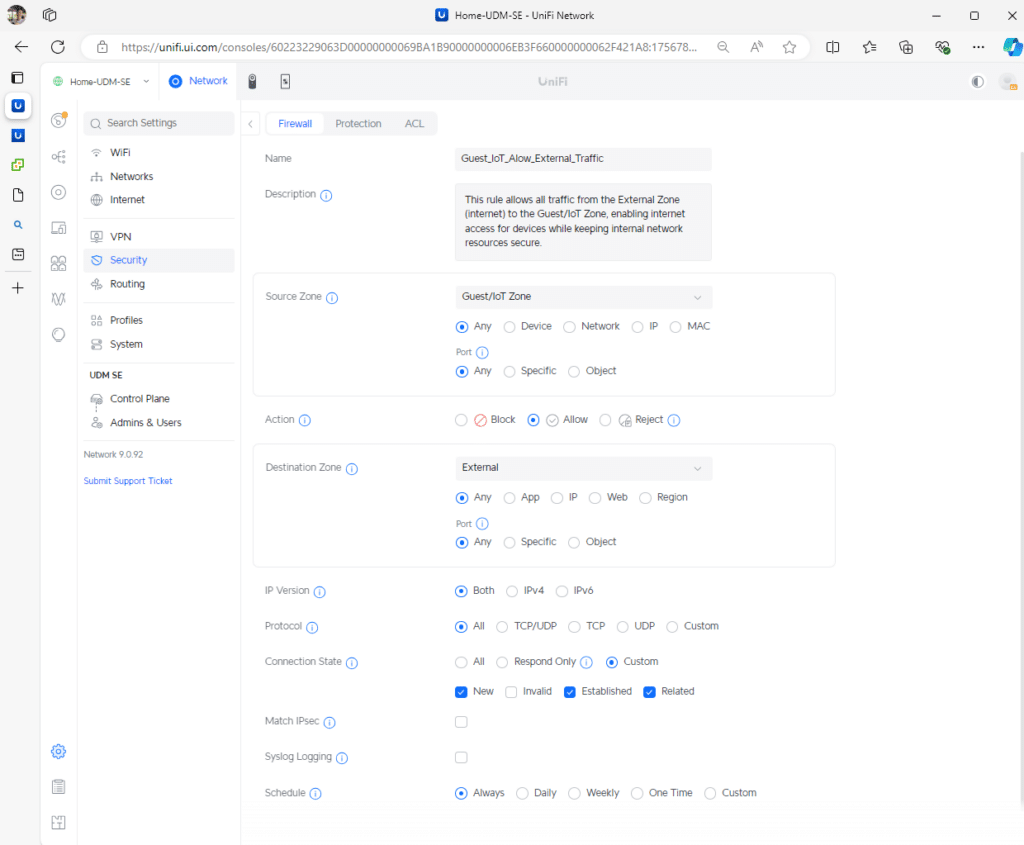
Rule2: Allow IoT/Guests to access the Internet via the External zone:
Rule3: Allow IoT/Guest to communicate with the gateway for DHCP and DNS via the Gateway zone.
Testing Rules
Once the rules have been created, we can proceed with testing. For this test, we will use an Ubuntu server 24.04.1 VM connected to a VNET network tagged with VLAN 30. The VM will pick up DHCP from the UDM-SE to confirm that the network configuration and zone rules are functioning as expected.
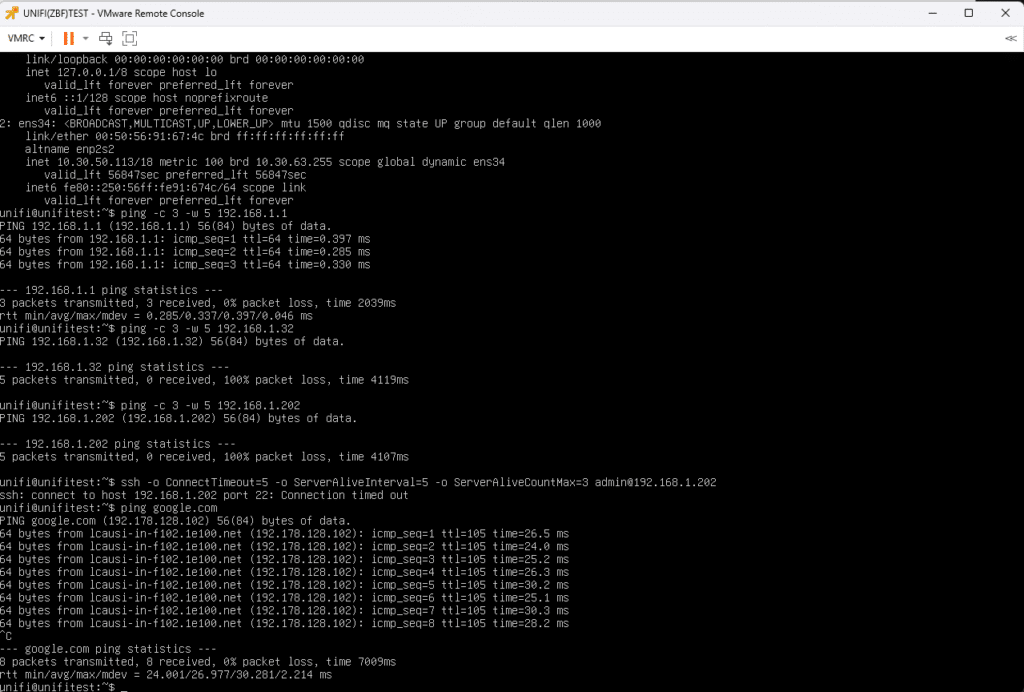
Starting with the command, ip a shows that the Ubuntu VM has successfully picked up a DHCP lease of (10.30.50.113) from the (10.30.0.0/18) network on VLAN 30. The first test verifies communication with the gateway, and we successfully ping the main UDM gateway (192.168.1.1).
Next, we ensure we are blocked from reaching any devices on the internal network. The attempt to ping a domain controller at (192.168.1.32) fails, and the same holds true when we try to ping a managed switch at (192.168.1.202). We attempted an SSH connection to the managed switch, which also failed, as a further test. This confirms that the isolation rule works as expected for the Guest/IoT zone.
Finally, test if the VM has external reachability by pinging Google, verifying that the Guest/IoT network can access the internet while remaining isolated from the internal network.
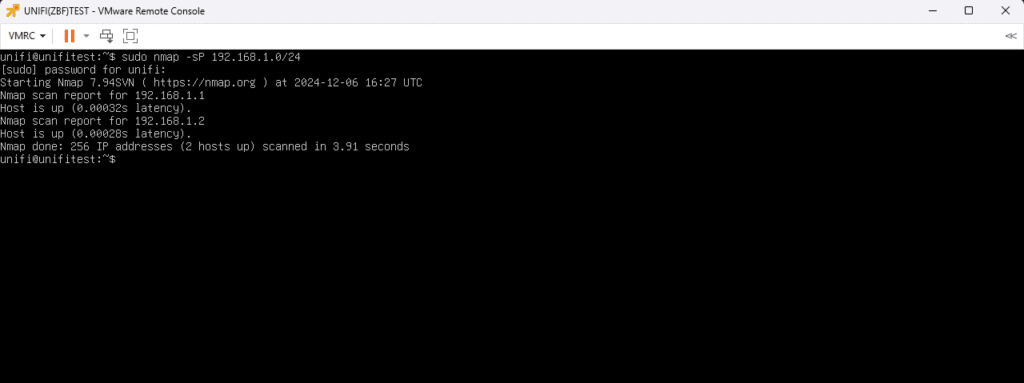
Nmap test
In this next test, we installed Nmap using sudo apt install nmap followed by the command sudo nmap -sP 192.168.1.0/24 to scan the default network range. Nmap is a network scanning tool that allows you to discover devices on a network and determine which ports are open on them. This test checks that the Guest/IoT network is properly isolated from the internal network by confirming that no devices in the 192.168.1.0/24 range are accessible from the isolated network.
Conclusion
UniFi’s new Zone-Based Firewall offers an intuitive and efficient approach to network security and segmentation. It’s a valuable asset for networks of all sizes, including labs like StorageReview, where professionals can leverage its capabilities. By simplifying the creation of isolated zones and enabling robust traffic control and secure VPN policies without the traditional complexities, this tool empowers administrators to design scalable, secure environments that support advanced testing, development, and daily operations.
Ubiquiti (affiliate link)





 Amazon
Amazon